Improving Human Resources (HR) Competence in the Information Systems and Technology Sector

Diponegoro University (Undip) held a Human Resources (HR) Competency Improvement Activity in the Information Systems and Technology Sector in 2025 from September 8-12, 2025. The event was opened by the Vice Rector III, closed by the Director of DSTI, and moderated by the Deputy Director of DSTI. Participants included Managers, DSTI Supervisors, DSTI staff, and […]
OneDrive Restrictions Circular
Undip Hosting Subdomain Registration
The unit submits a letter to the Director of DSTI with an attached SPTJM (Submission Report) and a copy to the Information Technology and Website Supervisor. The SPTJM template can be downloaded from the following link.
DSTI Wins Clean-Up Competition

In every grain of dust lifted,there’s a sincere intention to keep the earth healthy.In every drop of sweat,there’s a passion to keep the environment breathing.Alhamdulillah, our hard work and unity have borne fruit.Thank you, everyone!
Diponegoro University’s August 17th Competition

It’s not about winning or losing, but the spirit of independence that burns in every step!
2FA vs MFA

2FA vs. MFA: Is your account secure enough with just two layers, or do you need more? Let’s understand the differences for stronger protection! Differences & When to Use 2FA vs. MFA What is 2FA (Two-Factor Authentication)?2FA is a subset of multi-factor authentication that requires users to enter exactly two different factors, usually:A password (something […]
How a VPN Works
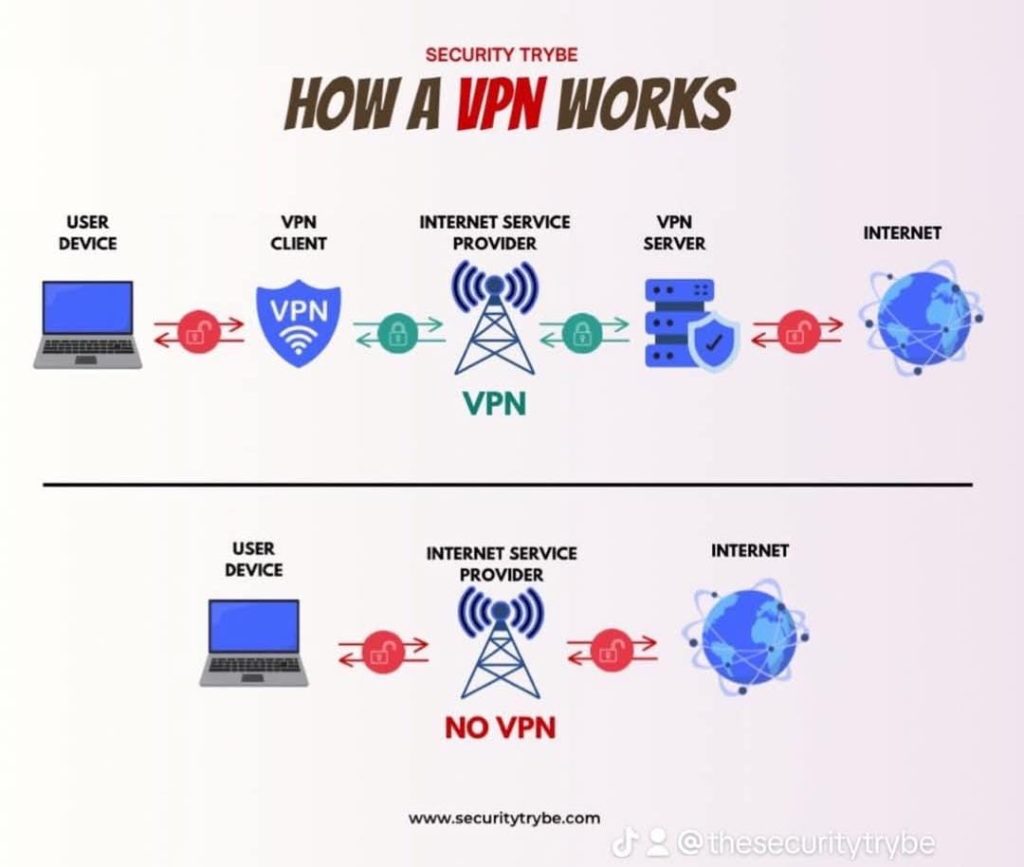
How a VPN works: Encryption and tunneling keep your data secure, while hiding your location and IP address. Activate a VPN to stay private online! Explanation: Illustration & How a VPN Works User Device → VPN ClientWhen you activate a VPN app on your laptop or phone, your device immediately establishes a secure connection to […]
Common Types of Password Attacks

Learn about five common types of password attacks, from brute force to credential stuffing. Protect your accounts with strong, unique passwords, and enable 2FA! Brute Force Attack: Hackers use automated software to try every combination of characters until they find the right one. This is very effective if the password is short or weak, but […]
Top Cyber Attact

Here are eight of the most frequently used types of cyberattacks, from phishing and malware to SQL injection, zero-day exploits, APTs, and ransomware. These are summarized to help you stay vigilant at all times. Phishing: A fraudulent attempt to impersonate a trusted party to steal sensitive data. Malware/Ransomware: A malicious program that steals data or […]
Workshop on the Use of Electronic Signatures (TTE) in the Faculty/School Environment of Diponegoro University in 2025,

Workshop on the Use of Electronic Signatures (TTE) in the Faculty/School Environment of Diponegoro University in 2025 which will be held on Thursday, June 12, 2025, at 09.00 WIB – finished in the Hall Room, 5th Floor, Dean’s Office, Faculty of Engineering, Undip Tembalang Semarang Campus, attended by the Deputy Director of Information Systems and […]

